isthisreal.io
Independent tool • Research & development
Published:
A privacy-first email scam and phishing signal checker built to help everyday users assess suspicious messages using explainable indicators, not opaque scoring. Visit the email checker case study to learn more about the email checker tool.
This case study reflects our approach to AI governance and quality engineering, detailed in our Services.
Note: This is an independent tool. Not client work.
.eml file.
Why we developed it
We built this tool to help reduce the incidence and impact of scam emails for everyday users. People receive suspicious emails constantly, but most don't have the technical background to interpret delivery metadata, authentication results, or header-level inconsistencies, even though that's often where the clearest risk signals sit.
Rather than an opaque “AI detector”, this is a signal-based checker designed to make warning signs understandable and actionable.
What this tool is trying to achieve
- Reduce harm through comprehension
- Surface explainable signals users can reason about
- Support judgement, not replace it
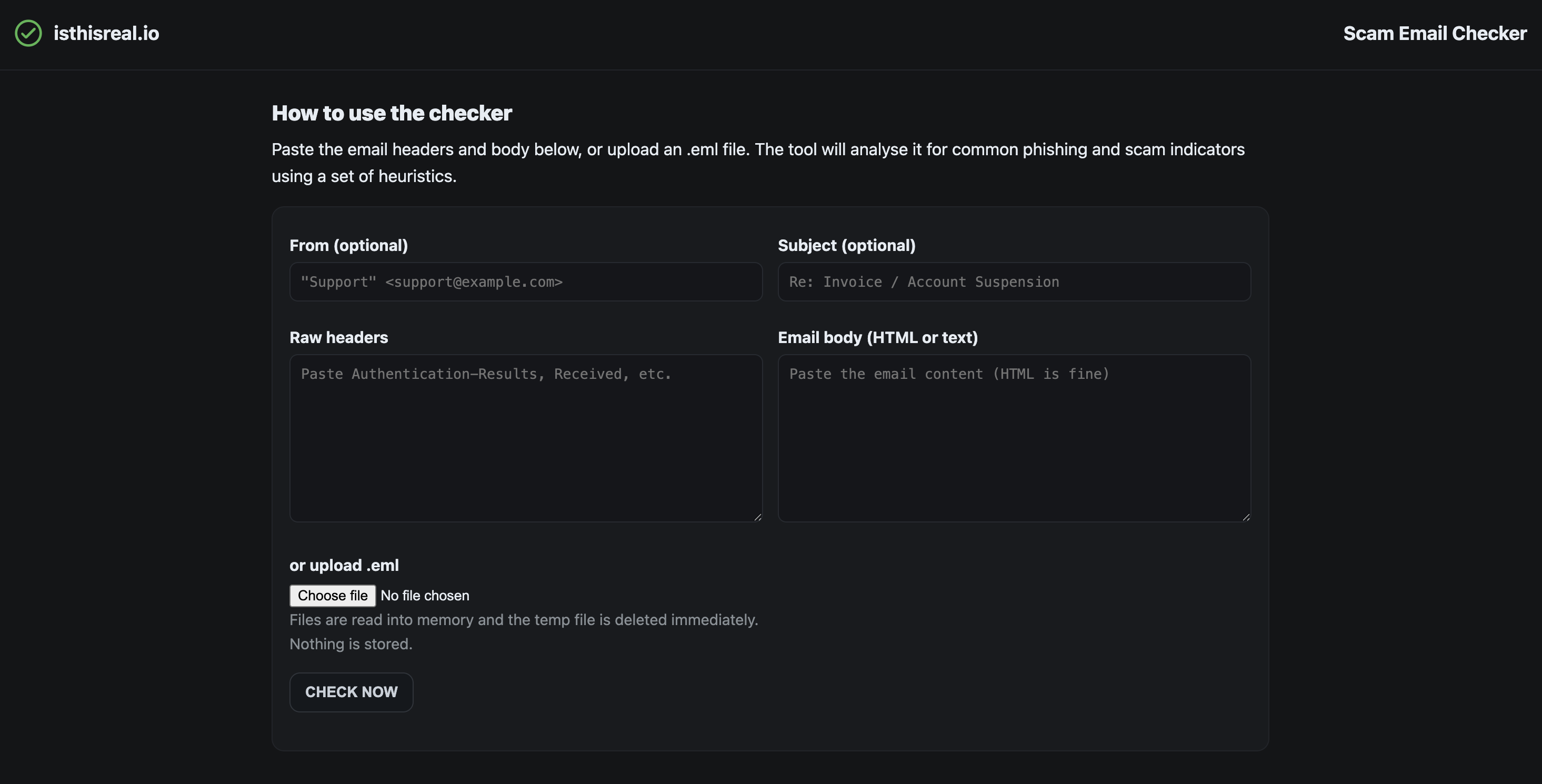
How to use the checker
- Paste the email headers and body into the form, or upload an
.emlfile. - If pasting manually, include headers like Authentication-Results and Received where available.
- Paste the email body as plain text or HTML.
- Review the surfaced indicators and decide your next step (delete, report, verify separately).
Tip: Never click links inside suspicious emails. Verify using a trusted, separate channel.
.eml preserves the original message structure for accurate analysis.
Design intent
What the tool does
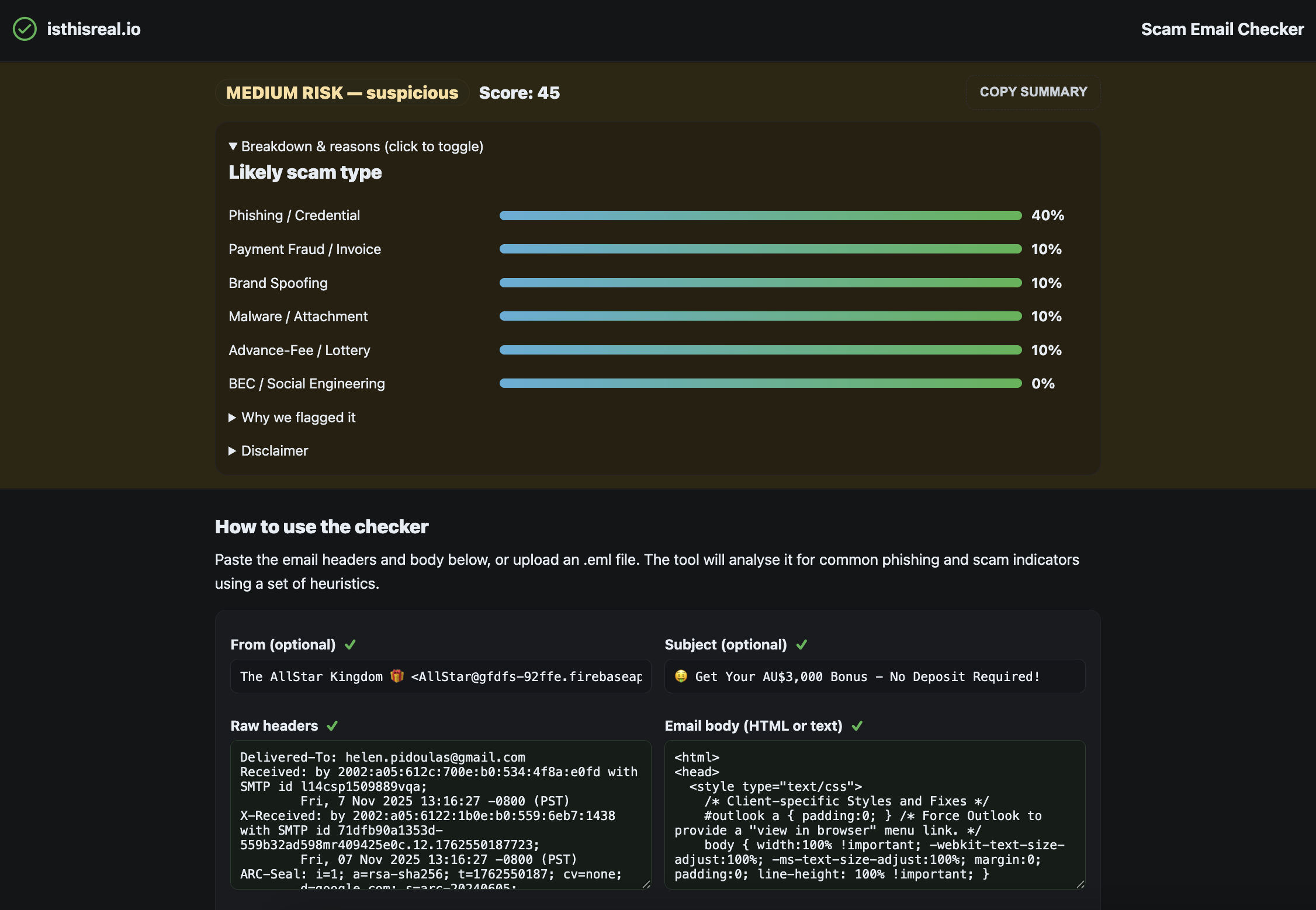
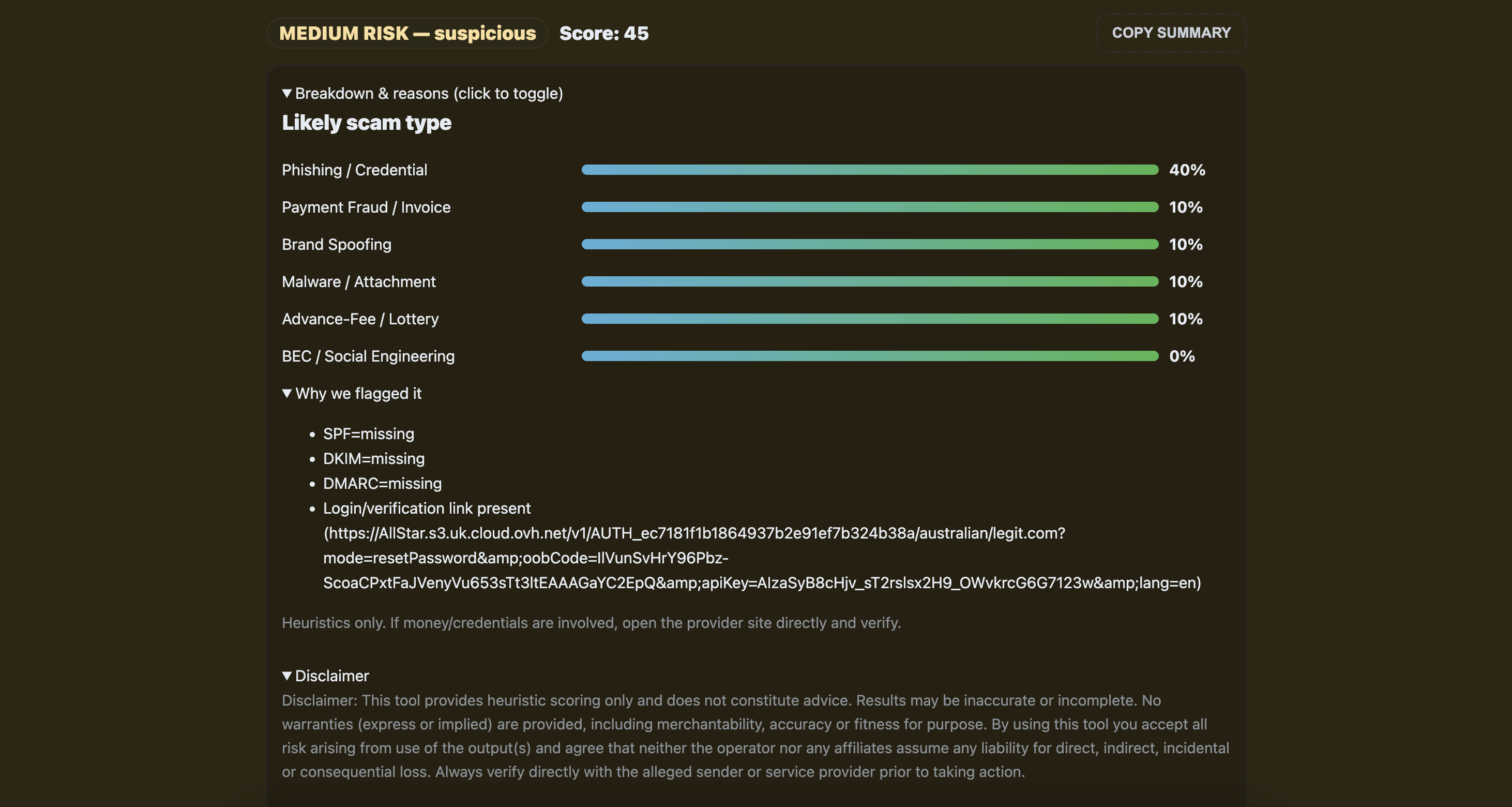
- Analyses phishing and scam indicators using defined heuristics
- Surfaces authentication and sender-identity inconsistencies
- Highlights delivery metadata patterns common in spoofing
- Flags content-level red flags (language, urgency, links)
- Runs entirely in memory
What it deliberately does not do
- Claim certainty or definitive verdicts
- Replace user judgement or professional investigation
- Rely on opaque or unexplainable scoring models
- Store, retain, or train on user data
Privacy & data handling
Files are processed in memory and any temporary file is deleted immediately. Nothing is stored.
- In-memory processing only
- No retention of uploaded content
- No storage of email headers or body
- Designed to minimise exposure of sensitive information
What this shows in practice
This project demonstrates applied thinking across digital trust, harm reduction, explainability, and privacy-first engineering, aligned with how Xyphos approaches governance-led delivery in regulated and high-risk contexts.
- Clear, auditable signals
- Human-centred risk communication
- Privacy as a design constraint, not an afterthought
- No “AI says so” claims
Research & references
Australian-based guidance
Technical background
Want governance-led delivery that holds up under scrutiny?
If you're operating in a regulated or high-risk environment and need practical controls, assurance, and delivery discipline, let's talk.